In the Part 1 of this series , we've had a look into the basic process involved in building the Zeus bot executable and customizing the Zeus configurations . In this part , we will dig deep inside the Zeus network communcations , its command and control activity and some of its more advanced features implemented for stealing user's identity.
Zeus Network Communications
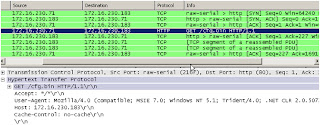
When the bot is executed in a virtual machine, initially, it communicates over the HTTP protocol and sends the GET request to the Command and Control server to retrieve the configuration file and the server replies with the requested configuration file. This request is made repeatedly on the basis of the timer value configured in the configuration file
Bot sends the information of the infected computer back to the control server according to the “url_server” parameter specified in the configuration file
Upon closer analysis of the Zeus network communications, we have come across an interesting similarity between the GET response from the server and the next POST request sent by the bot.
As observed above, this similarity is spotted in the initial part of the GET response from the server and the POST request from the bot. i.e starting at the 3rd byte after the HTTP header ends. We have had similar observations with all the older versions of Zeus bot. This is something which can be used to implement the generic detection for this bot on a network gateway!
HTML injection on SSL secured banking transactions
As the banking websites evolved, they have added extra layer of security in order to mitigate the keystroke logging attacks. On the other hand, continuously evolving malwares have also come out with new techniques to bypass these security measures and steal the login credentials. Password stealing botnet such as Zeus now use HTML code injection techniques whereby bot on the infected computer injects HTML code into the legitimate web pages of the banking site to request additional personal information not required during the transactions. This entices the users to input more credentials than required, which is captured by the bot and posted back to the Zeus bot masters command & control server.
Before injecting into HTML pages, the targeted site looks like this
After injecting into HTML page, same targeted site looks like this.
This shows how even forms that are supposed to be HTTPS encrypted can be manipulated by a bot to entice the user into typing out arbitrary levels of personal information, that can be then captured (using key logging) and sent off to the C&C master.
The basic injection HTML mechanism involved over here is , When a machine gets infected with Zeus , it will wait and watch your web surfing activity . It sits inside your Operating System and hooks several Windows APIs to intercept the website access over HTTPS .
Above screenshot just shows that . It modifies the memory of the several Windows process , creates pages inside it and then injects its own code to intercepts user's communication .
When user is found accessing one of the targetted banking website , it intercepts the activity and after the page is decrypted on the host machine , it uses following web injection template in the file webinjects.txt to inject the code .
It is clearly visible that all the code between the tag data_inject is the one that is injected into Web page .
Intercepting mouse clicks and capturing virtual keyboard screenshots
Banking websites have come up with the Virtual Keyboard technique in order to mitigate the keystroke logging attacks . Zeus counter-attacks this security feature by capturing the screenshots on each mouse click . Each click will be intercepted and a screenshot captured which will be sent to the drop server which is then combined sequentially to extract the entered password as shown below.
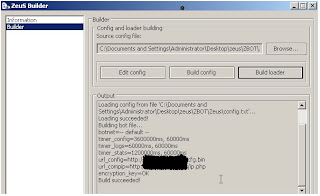
Analysis of the decrypted configuration file
Once the machine is infected with the Zeus bot, you can use the Zeus Decoder tool available here to decrypt the encrypted config file. Let‘s take a look at the decrypted config file. We’ll see the HTML injection code that this bot has added into it
http://172.16.230.183/cfg.bin
http://172.16.230.183/ip.php
http://172.16.230.183/bt.exe
http://172.16.230.183/gate.php
!*.microsoft.com/*
!http://*myspace.com*
https://www.gruposantander.es/*
!http://*odnoklassniki.ru/*
!http://vkontakte.ru/*
@*/login.osmp.ru/*
@*/atl.osmp.ru/*
https://banking.*.de/cgi/ueberweisung.cgi/*
*&tid=*
*&betrag=*
https://internetbanking.gad.de/banking/*
KktNrTanEnz
https://www.citibank.de/*/jba/mp#/SubmitRecap.do
SYNC_TOKEN=*
https://www.mybank.com/loginform.asp --> Fake banking website that we added while building the config file
HTML Injection code in the config file:
Following is the abbreviated list of banking websites found in the decrypted configuration file . This is just a partial list of websites .
https://online.wellsfargo.com/signon*
https://www.paypal.com/*/webscr?cmd=_account
https://www.paypal.com/*/webscr?cmd=_login-done*
https://www#.usbank.com/internetBanking/LoginRouter
https://easyweb*.tdcanadatrust.com/servlet/*FinancialSummaryServlet*
https://www#.citizensbankonline.com/*/index-wait.jsp
https://onlinebanking.nationalcity.com/OLB/secure/AccountList.aspx
https://www.suntrust.com/portal/server.pt*parentname=Login*
https://www.53.com/servlet/efsonline/index.html*
https://web.da-us.citibank.com/*BS_Id=MemberHomepage*
https://onlineeast#.bankofamerica.com/cgi-bin/ias/*/GotoWelcome
https://online.wamu.com/Servicing/Servicing.aspx?targetPage=AccountSummary
https://onlinebanking#.wachovia.com/myAccounts.aspx?referrer=authService
https://resources.chase.com/MyAccounts.aspx
https://bancaonline.openbank.es/servlet/PProxy?*
https://extranet.banesto.es/*/loginParticulares.htm
https://banesnet.banesto.es/*/loginEmpresas.htm
https://empresas.gruposantander.es/WebEmpresas/servlet/webempresas.servlets.*
https://www.gruposantander.es/bog/sbi*?ptns=acceso*
https://www.bbvanetoffice.com/local_bdno/login_bbvanetoffice.html
https://www.bancajaproximaempresas.com/ControlEmpresas*
https://www.citibank.de*
https://probanking.procreditbank.bg/main/main.asp*
https://ibank.internationalbanking.barclays.com/logon/icebapplication*
https://ibank.barclays.co.uk/olb/x/LoginMember.do
https://online-offshore.lloydstsb.com/customer.ibc
https://online-business.lloydstsb.co.uk/customer.ibc
https://www.dab-bank.com*
http://www.hsbc.co.uk/1/2/personal/internet-banking*
https://www.nwolb.com/Login.aspx*
https://home.ybonline.co.uk/login.html*
https://home.cbonline.co.uk/login.html*
https://welcome27.co-operativebank.co.uk/CBIBSWeb/start.do
Botnet Command and Control
This toolkit comes with a Control panel installation which is typically used to track the botnet infections. This is a PHP application which can be run on a Web Server along with the other required database software (MYSQL). It also enables the attacker to remotely control and send commands to Victim’s computer.
I opened one of the scripts that came with this toolkit and I found the Bot can be given following commands:
-------------------------
$_COMMANDS_LIST = array
(
'reboot' => 'Reboot computer.',
'kos' => 'Kill OS.',
'shutdown' => 'Shutdown computer.',
'bc_add [service] [ip] [port]' => 'Add backconnect for [service] using server witn address [ip]:[port].',
'bc_del [service] [ip] [port]' => 'Remove backconnect for [service] (mask is allowed) that use connection to [ip]:[port] (mask is allowed).',
'block_url [url]' => 'Disable access to [url] (mask is allowed).',
'unblock_url [url]' => 'Enable access to [url] (mask is allowed).',
'block_fake [url]' => 'Disable executing of HTTP-fake/inject with mask [url] (mask is allowed).',
'unblock_fake [url]' => 'Enable executing of HTTP-fake/inject with mask [url] (mask is allowed).',
'rexec [url] [args]' => 'Download and execute the file [url] with the arguments [args] (optional).',
'rexeci [url] [args]' => 'Download and execute the file [url] with the arguments [args] (optional) using interactive user.',
'lexec [file] [args]' => 'Execute the local file [file] with the arguments [args] (optional).',
'lexeci [file] [args]' => 'Execute the local file [file] with the arguments [args] (optional) using interactive user.',
'addsf [file_mask...]' => 'Add file masks [file_mask] for local search.',
'delsf [file_mask...]' => 'Remove file masks [file_mask] from local search.',
'getfile [path]' => 'Upload file or folder [path] to server.',
'getcerts' => 'Upload certificates from all stores to server.',
'resetgrab' => 'Upload to server the information from the protected storage, cookies, etc.',
'upcfg [url]' => 'Update configuration file from url [url] (optional, by default used standard url)',
'rename_bot [name]' => 'Rename bot to [name].',
'getmff' => 'Upload Macromedia Flash files to server.',
'delmff' => 'Remove Macromedia Flash files.',
'sethomepage [url]' => 'Set homepage [url] for Internet Explorer.'
-------------------------
Amazing stuff !!..Quite a few prety decent commands implement in this bot . I spent some time installing PHP and MySQL after installing the Webserver and this is how the Zeus control panel looks like .
Very neat installation steps . It will asks you to configure Root user to administer the control panel , Mysql server username and password , local folder for reports , encryption key to decrypt the RC4 encrypted HTTP communications etc. and that's it ..You are ready to go !!.
Detecting Zeus Botnet on the Wire
This blog would remain incomplete without talking about the ways to detect Zeus botnet on the wire . One of the more obvious way to detect this bot is to correlate the GET response from the server and POST request from the bot client as we saw earlier in this post . But this method of detecting is rather very expensive in terms of performance and is expected to consume high memory as we are not inspecting or comparing the payload against any constant pattern of bytes .
Another method is perhaps the more decent heuristic to detect the fishy activity with the banking sites . Idea is to detect the change in the number of HTML form fields while accessing the banking site and when the data is posted back on the server . This can be detected on the Network gateway . In the case of Zeus
Hope you 've had fun reading this analysis series :)