During the December last year , a critical
vulnerability was identified in Adobe Reader X / Adobe Acrobat X version
10.1.1 and earlier for Windows and Mac OS , Adobe Reader 9.4.6 and Adobe Reader 9.x versions for Unix . This was a 0 day vulnerability (CVE-2011-2462) potentially allowing an attacker to execute arbitrary code and take the control of victim machine without user knowledge
Analysis of the PDF 0 day exploit
I analysed in
the exploit PDF with MD5 : b025b06549caae5a7c1d23ac1d014892,
that I received few days back. The
technique used in this exploit has been known to the researchers since the ages.
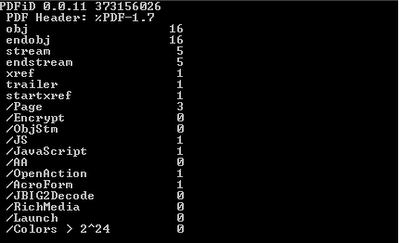
Let’s check what we get
as the output when we run PDFiD tool against this exploit.
Looking at the output of
the PDFiD , we can rightaway make out on what this exploit would contain
within. As with a lot of other exploits in the wild, this document uses the
technique of /JavaScript and /OpenAction to launch the malicious javascript .
The combination of both these make this document suspicious to an eye of the
researcher.
/JS and /JavaScript indicates that this pdf
document contains the javascript while the /OpenAction indicates the action to be performed
automatically when the document is viewed
Let’s take the deeper look at the
object structure of the pdf document and find out what is interesting to us
Object Analysis of the PDF document
Just to get back to some basics , you might already
know , pdf dictionary objects starts with the keyword obj and end with endobj while
pdf stream dictionary objects starts with the stream and ends with endstream
keywords
Object 4 has the /OpenAction
reference to the object 14 which seems
particularly interesting. Lets take a look at what’s out there
in the referenced object
Object 14 as seen in above has
the stream link to object 15 which contains the actual compressed javascript
This is the malicious
javascript that is encoded twice, first with ASCIIHexDecode and then with
FlateDecode. These stream filters will indicate
Adobe Reader on how to decode the streams while opening the document.
This combination of stream filters is widely used in exploits to compress the
code. We’ll take a look at the JS code little later in the Analysis . In the
meantime , let’s move further in the
object structure analysis of the pdf document.
document is rendered
As per the Adobe 3D Annotations documentations available here, , 3DD entry of the Annotations data specifies the FlateEncoded Data stream containing the U3D data. That’s exactly what we see in Object 10 as shown below
This U3D data is likely
to cause the memory corrupution and trigger the vulnerability Moving to the
last Object 16 is of special interest to
us. Let’s check how this object looks.
This object does not have any references and contains
the stream that is supposed to be FlateEncoded. It is this stream which
contains the malicious XORed executable that is dropped after successful
exploitation. Let’s see if we can figure out the XOR key.
Executable has been XORed
by 0x12 . Looks like this stream wasn’t FlateEncode but rather simply XORed to embed
the malicious file within. This techniques are normally used in exploits to hide
the malicious code and thereby bypassing the AV detections.
Let’s take a look at the decoded JS code from Object 15 to understand what it
does.
This code is checking for supposedly non-existant versions of the Adobe Reader and apparently enters the infinite loop if the version comes out to be greater than 10.0 . This code used the heap spray technique to exploit this vulnerability and execute the shellcode. End of this code is checking for the Windows platform and sets the document to page 2 if it is running on the Windows platform which will render the 3D data specified by the U3D file causing the corruption.
The actual heap spray function in the JS code looks like this :
Last function call in the above figure is the one that
allocates the memory and fills up the heap as seen below.
Launching this exploit on the Windows platform with
Adobe Reader 9.4.6 installed , it will crash and open the new document 2012
Federal Employee Pay Calender.pdf .
Spawning the new process pretty.exe and finally injecting the
WSE4EF1.TMP.dll in iexplore.exe proces which then connects to the command &
control server.
Looking at the code of
the pretty.exe
we’d see that it looks for outlook.exe, iexplore.exe, and firefox.exe. It then injects
the code into whichever process it finds open on the victim machine.
Network
Communications
While the server responded HTTP 301 with the location header having the HTTP link

After which HTTP GET request initiated looks like as shown below . The URI query string contains the parameter which is the hostname of the victim machine appended along with the IP address.
Looking at the injected
dll , following code forms the HTTP GET request along with the URI query
parameters
Further analysis of the
command & control code of the sample reveals that the following commands
can be given to perform the respective actions on the victim system.
Cmd ,Shell , Run , Getfile, Putfile, Kill, Process, Reboot, Time, Door





















No comments:
Post a Comment